Introduction
Usually Jenkins master and Jenkins agent are located in the same network, therefore it is quite easy to adopt Jenkins agents using SSH. This time we will talk about situation when Jenkins master and bunch of other DevOps tools are running in "network A" and Jenkins agents are running in "network B". Quite often connections from A to B are rejected, however connections from B to A are accepted. There might be various reasons, in general network B has elevated security expectations. Typical setup is Jenkins master located in public cloud and Jenkins agent(s) located in private customer network. Private customer network might be needed in such because some sort of higher data privacy requirements must be matched or some specialised hardware is present in customer premises and it cannot be accessible directly from public internet.
Solution
Recommended solution is master/agent setup, when master runs in public environment and agent is running on server located in private network. Agent is also called "on premise executor" (OPE). Jobs are then performing jobs/tasks on such agent in internal/private networks. Jenkins Agent has active connection from internal network to internet accessible Jenkins Master via recommended JNLP port tcp/9000 and keeps listening to builds/jobs. Port can be changed, but we will keep talking about 9000. NO direct or NAT network connection is required from internet to internal network. It is secure and simple solution.
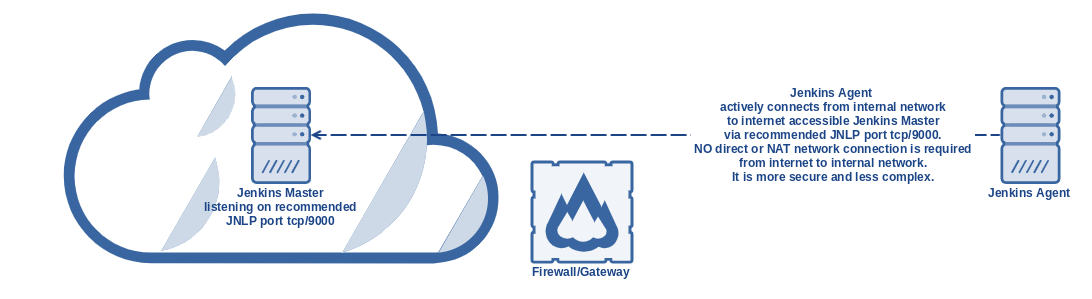
Requirements:
- Jenkins master running in public and listening on JNLP port tcp/9000
- firewall opening for port tcp/9000 from source agent(s) IP(s) in internal network towards internet in general (destination 0.0.0.0)
- servers running in internal network(s)
- Jenkins agent service(s) with agent service auto-start to assure automatic re-connect to Jenkins master at any time